Since the support of goo.gl has already ended, I’ve been looking for ways to shorten URLs using Google services.
Some time ago I found a bug that allowed me to shorten links using Google’s official g.co shortener.
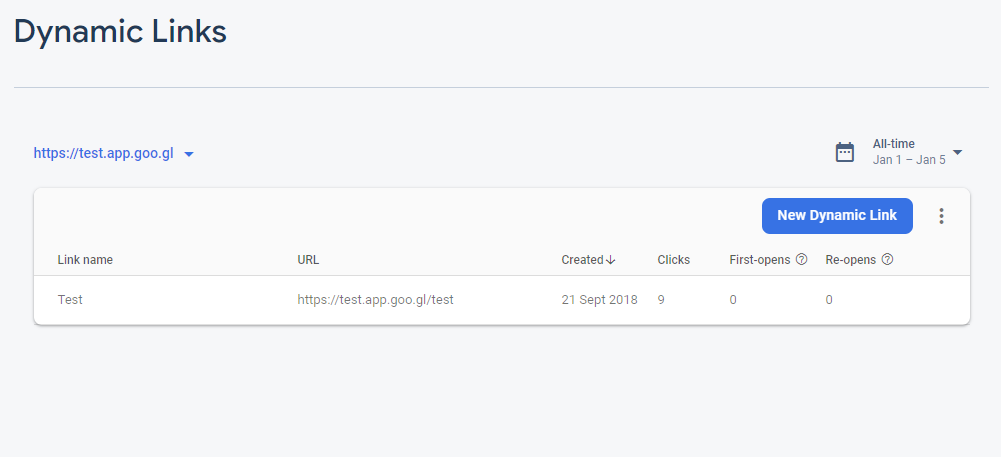
This time I took a look at Firebase Dynamic Links.
Firebase Dynamic Links
They work by allowing you to create short URLs on either *.app.goo.gl or *.page.link subdomains.
Before app.goo.gl subdomains in Firebase were discontinued, there was a randomly generated app.goo.gl subdomain for each Firebase project, something like i63lqb.app.goo.gl. It could also be accessed via goo.gl/app/i63lqb/ourLink (= i63lqb.app.goo.gl/ourLink on mobile devices).
You could also create four more *.page.link subdomains, but this time you could choose your own subdomain.
Setting up a new subdomain
When I was setting up a new subdomain I noticed an interesting API call.
/v1/checkValidDomainForProjectThis returned an OK response in case the subdomain I wanted to create was both valid and not already in use. In case it was OK, the Create button was enabled and I was able to create it. Otherwise, it showed an error.
Once I clicked the button to create it, another API call was fired, this time to:
/v1/createDomainForProjectalso containing the desired subdomain in its body.
If I let the POST call through, it would successfully add the subdomain to my project.
But let’s go back to the last API call. Since we know there are two types of domains we can use to shorten links in Firebase, let’s try to replace the value of the domainUriPrefix parameter from page.link with app.goo.gl.
Surprisingly, this actually worked. A <myCustomPrefix>.app.goo.gl subdomain was added and could be used in the project.
Since custom *.app.goo.gl subdomains like maps.app.goo.gl or news.app.goo.gl are used only for official products by Google, they should be registered only by them.
This leaves us with the following attack scenario:
A regular user can create custom subdomains on app.goo.gl via the Firebase Console. This should be possible to do only by Google.
| Timeline | |
|---|---|
| 2018-08-10 | Vulnerability reported |
| 2018-08-13 | Priority changed to P1 |
| 2018-08-14 | Accepted |
| 2018-08-22 | Fixed |
| 2018-08-29 | Reward issued |